


Phishing has always been around. What’s changed is the quality. The sloppy tells are gone, so the emails that hurt you look like normal work: a vendor thread, an invoice update, a “reset my access,” a calendar invite that lands right on someone’s schedule. This is now a business email compromise (BEC) problem as much as a phishing problem. Then the same loop starts: “is this legit?” forwards, finance pressure, and security taking the blame when one message slips through.
Before you add another security product, it’s worth asking a simpler question:
Have we pushed Microsoft 365 / Google Workspace as far as they can go — with native controls?
This guide is the raise-the-floor playbook: make external email unmistakable, tighten authentication signals (SPF/DKIM/DMARC), remove dangerous trust gaps, and add friction to high-risk requests.
The second half of this guide includes post-click admin wins (OAuth consent, auto-forwarding, legacy auth, device trust, phishing-resistant MFA).
Admins and security teams responsible for Microsoft 365 email security (Exchange Online, Defender for Office 365, Entra ID) and/or Google Workspace Gmail — especially if you’re evaluating email security services or an email security gateway and want to harden native controls first.
If you only do a few things:
This is the boring win that actually matters: restore a fast visual truth.
“This message is from outside the organization.”
Invites are a “quiet bypass” — they can land as calendar noise where users don’t apply normal inbox scrutiny.
A. Google Workspace (admin-friendly lever): You can set the org default for what invites get auto-added. One option is “Invitations from known senders,” where unknown senders only reach users via email.
Verify: send an invite from an unknown external sender and confirm it doesn’t auto-appear on the calendar (the user receives an email invite instead).
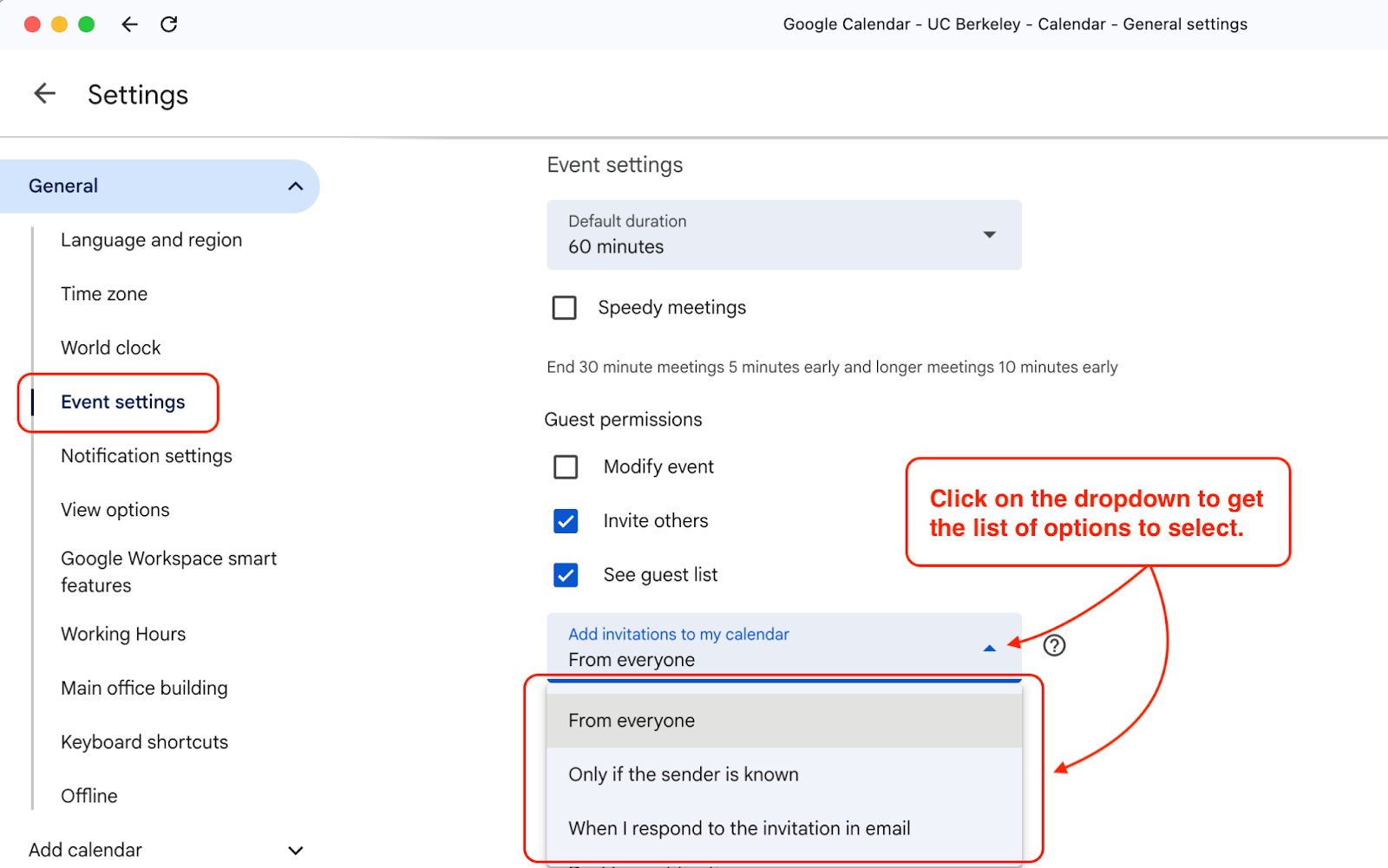
B. Microsoft 365 (practical lever): mail flow rule for Calendaring messages:
Set-CalendarProcessingis documented as effective only on resource mailboxes (rooms/equipment), so treat “turn off auto-processing everywhere” advice as advanced and test carefully.
Instead, if you’re seeing spammy external invites, you can use an Exchange mail flow rule that targets message type = Calendaring and external senders to remove or divert those messages.
Verify: send an external meeting request > confirm it’s blocked/diverted per your rule.
There are two approaches. Most orgs do both: a native indicator for everyone, and a louder banner for high-risk groups.
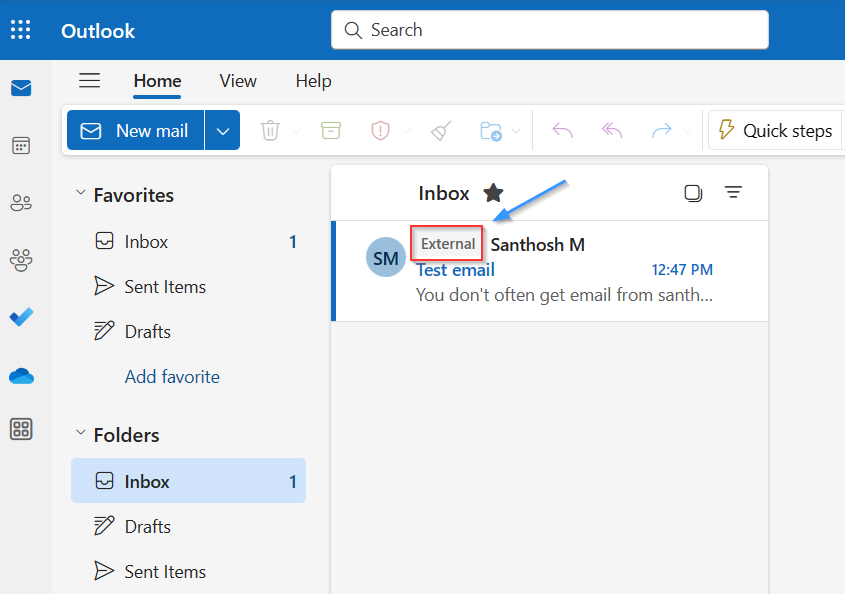
Microsoft supports a native “external sender identification” UI in Outlook clients, enabled tenant-wide via Exchange Online PowerShell.
Commands:
Set-ExternalInOutlook -Enabled $true
Get-ExternalInOutlook(These cmdlets specifically control external sender identification in Outlook, OWA, Outlook for Mac, and mobile clients.)
Verify: send an email from outside the tenant and confirm the external sender callout appears in Outlook.
A mail flow rule (transport rule) is an “if/then” rule for messages. Microsoft documents using the EAC “Apply disclaimers” action > add organization-wide disclaimers/headers/footers.
EAC path: Mail flow > Rules > Add rule > Apply disclaimersWhen to use: Finance/AP, exec assistants, or any group that routinely processes money/access requests.
Keep the banner short:
External sender — don’t approve payment or password requests without verification.
Verify: external test email triggers the banner exactly once (avoid banner duplication loops).
Two layers:
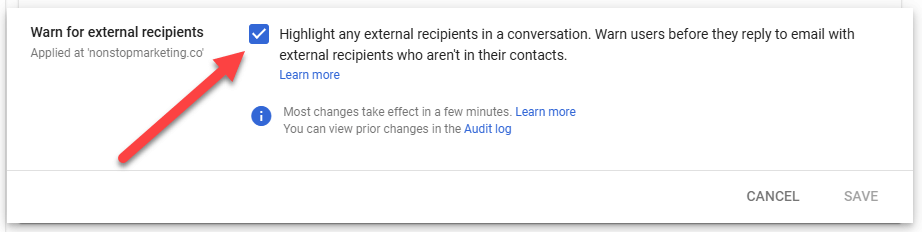
Verify: send test threads involving external participants and confirm the intended warning behavior; confirm advanced protections are set for high-risk groups.
If you need custom “tripwire” behavior (banner, route to review mailbox), use Gmail compliance content filtering rules.
Most orgs have SPF. Fewer have DKIM + DMARC fully implemented and enforced.
Minimum bar:
Editor’s note: we will do a deeper dive in DMARC rollout post next
AI phishing works best inside trusted stories (“your vendor,” “your bank,” “your payroll provider”). Broad allow-lists make that easy.
Microsoft 365: audit transport rules and any allowlisting. Microsoft’s guidance on allowing inbound messages exists, but the key idea is: avoid wildcards and scope to real workflow senders.
Google Workspace: use address lists and compliance/routing settings carefully — avoid giving “always allow” status to entire domains unless you can justify it.
Operational policy (worth saying explicitly):
Bank detail changes and payment releases are never approved on email alone.
You’re not trying to catch every scam with keywords. You’re encoding a short list of scenarios that should never be frictionless.
Microsoft 365: mail flow rules support conditions/exceptions to target high-risk patterns (e.g., external sender + finance recipients + “wire instructions / ACH update”).
Google Workspace: implement narrow rules with Gmail compliance content filtering (banner, route a copy to a review mailbox, etc.).
If you want these tripwires to actually hold risky mail (vs just warn), use a mail flow rule action that sends the message to quarantine.
Where: Exchange admin center to Mail flow to Rules
Rule pattern: If external sender + finance recipients + payment keywords send to quarantine
Recommended “bank change / wire” rule
wire, ACH, routing number, bank details, invoice updateImportant gotcha (worth calling out in the post):
When a rule sends a message to quarantine, rule evaluation stops, and if the message is later released, the rules that weren’t evaluated won’t run. So keep quarantine rules late in your rule order (or make them as self-contained as possible).
When to use “Review mailbox” instead of quarantine
Google’s cleanest “tripwire to hold for review” path is a Content compliance rule with the action Quarantine the message.
Prereq (one-time): create the quarantine
Then: create the tripwire rule
wire, ACH, bank details, etc.)You did the “keep threats out of the inbox” work. Now assume reality: one message gets through. Attackers typically try to do two things fast:
These controls make “one click” a lot less catastrophic.
Attack pattern: user approves a malicious OAuth app > attacker gets durable access without repeated logins.
Microsoft (Entra ID)
Google Workspace
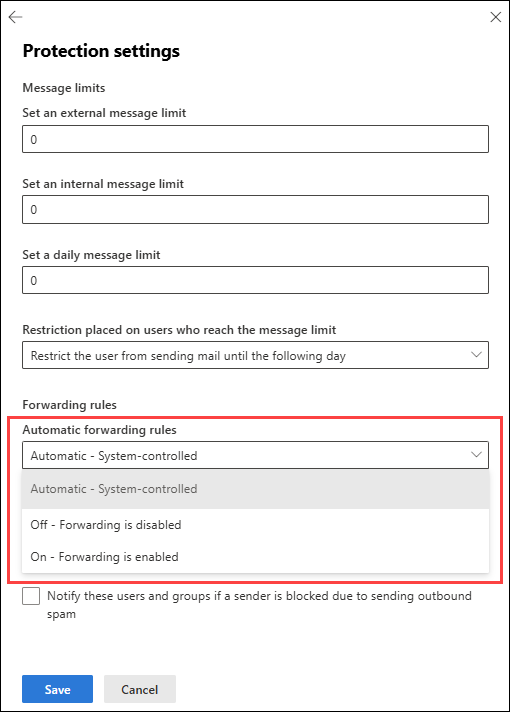
Attack pattern: account takeover > auto-forward > a personal mailbox > quiet data siphon.
Microsoft 365
Microsoft explicitly calls out that outbound spam policies control both Inbox rules forwarding and mailbox (SMTP) forwarding, and documents the three settings:
Config: Defender portal > Policies & rules > Threat policies > Anti-spam > Outbound spam policy > set Automatic forwarding = Off.
Verify: create an inbox rule that forwards externally > confirm it fails.
Google Workspace
Admins can turn automatic forwarding on/off for the org; when off, the forwarding option isn’t available in Gmail settings.Admin console > Apps > Google Workspace > Gmail > End User Access > Automatic forwarding > uncheck “Allow users to automatically forward…” (when off, the forwarding option disappears for users).
Verify: turn it off for an OU and confirm users can’t enable forwarding in Gmail settings.
Attack pattern: attackers create rules to hide replies, delete security notices, or reroute invoices.
Microsoft provides Defender XDR playbooks for investigating:
Verify: your team can find these alert types and has a runbook/owner (even if you don’t generate them in prod).
Attack pattern: password spraying against legacy protocols.
Microsoft documents a Conditional Access policy to block legacy authentication (further reading), starting in Report-only mode.
Verify: run report-only, review impact in sign-in logs, then enforce (exclude break-glass).
Editor note: this is a security default for all new tenants
Attack pattern: attacker logs in from a random unmanaged device.
Microsoft: Conditional Access can require “device marked compliant” (Intune-backed).
Verify: attempt access from an unmanaged/non-compliant device and confirm block/step-up behavior.
Google: Context-Aware Access lets you gate access based on device security status/location/IP; it’s edition-dependent.
Verify: create an access level, set to monitor first, then enforce for Gmail and validate on a test device.
Microsoft: number matching is documented as a security upgrade for Authenticator push.
For phishing-resistant MFA, Entra supports authentication strengths and recommends phishing-resistant methods like passkeys (FIDO2).
Passkeys (which use the FIDO2 standard) are considered phishing-resistant because, unlike passwords or one-time codes, they are cryptographically bound to the specific website or application they were created for. This feature defeats the central mechanism of phishing, which relies on tricking a user into giving up a transferable credential on a malicious site.
Verify: confirm number matching prompts are in use; pilot phishing-resistant MFA for a high-risk group with Conditional Access.
Google: admins can deploy/enforce 2-Step Verification and there’s an “Only security key” policy option.
Verify: apply to a test OU/group and confirm enforcement behavior.
Microsoft documents the built-in Report button and configuring it via user reported settings in Defender.
Verify: confirm the Report button appears for supported Outlook clients and reports land in your chosen destination (Microsoft, a mailbox, or both).
The “Report” button is only useful if reports land somewhere actionable and you treat them as an early-warning sensor.
What you want:
Microsoft 365
Google Workspace
Verify (5 minutes):
Use this as your “done” definition.
Bonus: Google calendar invite behavior set to “known senders” to prevent spam auto-adds.
Q: Is this enough without a third-party tool?
A: For many orgs, raising the native floor + identity containment removes the easy wins attackers rely on. If you still see targeted BEC or token abuse, then you evaluate additional layers.
Q: What should the follow-on post be?
A: “Assume one gets through: Identity & device hardening in Entra ID and Google Workspace” (phishing-resistant MFA for admins/finance, Conditional Access/Context-Aware Access, OAuth consent governance, and alert/runbook setup).
Q: Can I block calendar invitation spam/phishing using native tools?
A: Yes, but it requires changing defaults. By default, both Google and Microsoft automatically place invites on your calendar, which spammers exploit.
Q: How do I detect hidden text (ZeroFont) or obfuscated links without buying new tools?
A: Native tools struggle to "see" hidden text directly, but you can flag the behavior associated with it.
Q: Are third-party AI security tools better than native Microsoft/Google defenses?
A: "Better" is the wrong metric; "different" is more accurate.
Q: What new AI-driven email scams should we look out for this year?
A: The landscape of AI email security is shifting—AI has perfected the 'boring' parts of phishing. Expect Deepfake Voice/Video in "Fake CEO" attacks (vishing) and Hyper-Personalized Phishing. Attackers use AI to scrape LinkedIn and write emails that reference specific recent events (conferences, deal closings) to build instant trust. The best defense is process, not just tech: require secondary verification (like a quick phone call) for any unusual payment request.