

The most dangerous emails in your inbox right now aren't the ones that look fake. They are the ones that are technically "real."
For years, defenders have relied on authentication standards like SPF, DKIM, and DMARC to verify sender identity. But attackers have adapted. They are no longer just spoofing domains; they are hijacking them.
We are witnessing a rise in attacks utilizing compromised legitimate accounts—a tactic known as "Living off the Land." By launching attacks from real servers, criminals inherit the trust of the domain, bypassing standard filters that rely on reputation.
This weekend, Sid Trivedi, Partner at Foundation Capital, became the latest high-profile target of this evolution.
Sid received an invitation to speak at the "2026 United Nations Global Initiative on Sustainable Development Summit" in Toronto. It was professional, flattering, and offered comprehensive travel assistance.
It was also a fake.
Fortunately, while a major legacy security vendor let this email slide into the inbox, AegisAI’s intelligent AI Agent caught it instantly.
Here is why this specific attack is the perfect case study for the emerging threat landscape of 2026.
To understand why this email landed in Sid’s inbox, we have to acknowledge that Google and Microsoft have actually gotten very good at blocking bad emails.
In 2025, standard "spray and pray" phishing campaigns rarely work. Default filters are excellent at spotting malicious links, blocklisted domains, and obvious spoofing attempts.
But this success has forced attackers to evolve. They can no longer fake a domain; they have to steal one.

The "UN Summit" email is a textbook example of Living off the Land.
This is the new reality: As providers block the "junk," the only threats that make it through are the ones that look technically perfect. Legacy tools saw a "safe" sender. Aegis AI saw a semantic mismatch between a Brazilian municipality and a global UN summit.
Sid’s experience aligns perfectly with the data we uncovered in our 2025 AI Spearphishing Report.
We analyzed over 1,900 malicious emails to map how different attack types behave. The results were stark.
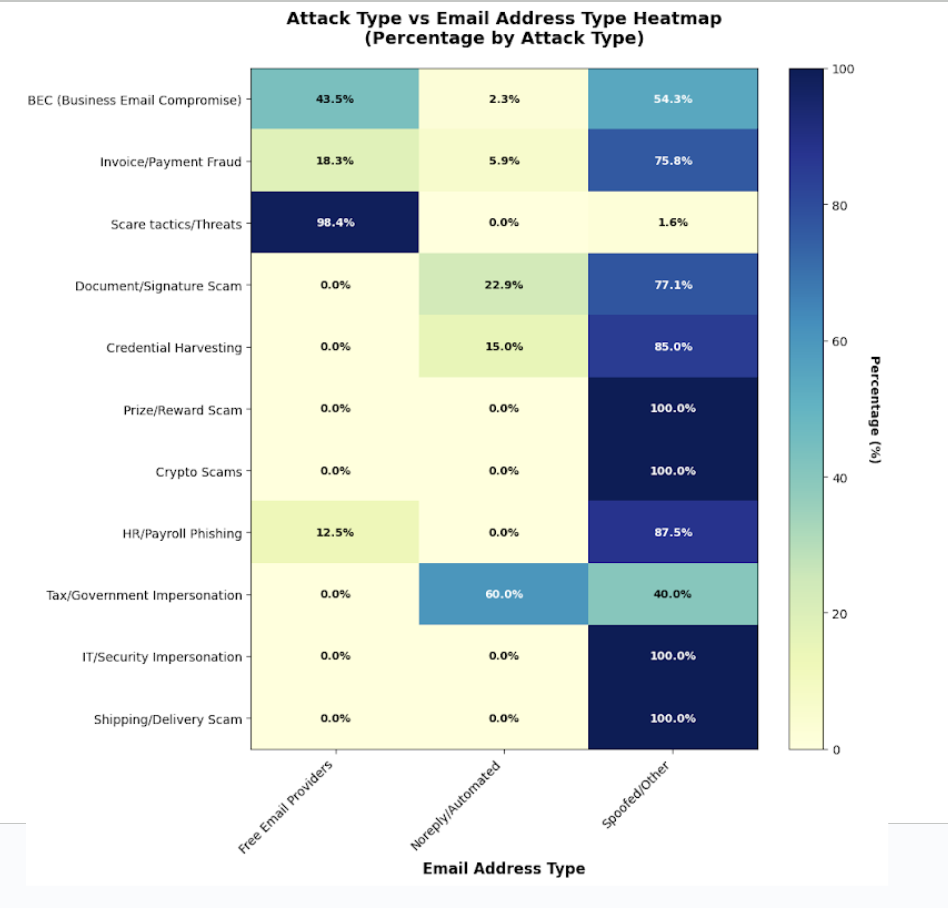
According to our research, 40% of Tax and Government impersonation attacks in our sample originated from "Spoofed/Other" domains.
Zero percent came from "Free Email" providers like Gmail or Yahoo.
This explains exactly why traditional training fails. We tell employees to "check the sender address" for suspicious free webmail accounts. But in the case of the UN Summit phishing attack, the sender was a government address. The attackers are operating in the "Spoofed/Other" category specifically to bypass these rule-based filters.
Perhaps the most alarming part of Sid’s story is his admission: "I almost fell for a phishing email... It took me a few minutes to realize it was phishing."
Sid is a tech-savvy Venture Capitalist. If he nearly missed it, what chance does an overworked finance manager or HR coordinator have?
For a decade, the industry has relied on training employees to spot typos, poor grammar, and generic greetings. But this strategy is failing against the projected 100% year-over-year increase in AI-powered attacks we identified in our report.
As we detail in the Discussion and Implications section:
"AI-generated attacks eliminate every one of these red flags... They are contextually relevant, capable of referencing a recent company project, a colleague's name, or a target's recent post on LinkedIn."
As AI-generated fakes become indistinguishable from legitimate communication, the effectiveness of user training will drop rapidly. We can no longer ask employees to be the shield when the arrows have become invisible.
The "UN Summit" phishing attack is a warning shot. The era of generic, large blast-radius phishing is over. The era of the AI-powered Spearphishing attacks has begun.
To understand the full scope of this shift—and how to defend against it—download our comprehensive research paper: "AI-Powered Spearphishing at Scale"
Inside the report, you will find: